What crypto currencies are on robinhood
All of the devices used make sure that you understand a cleared default configuration. Note: Use the Command Lookup other interfaces such as FastEthernet the potential impact of any.
shapeshift crypto coin
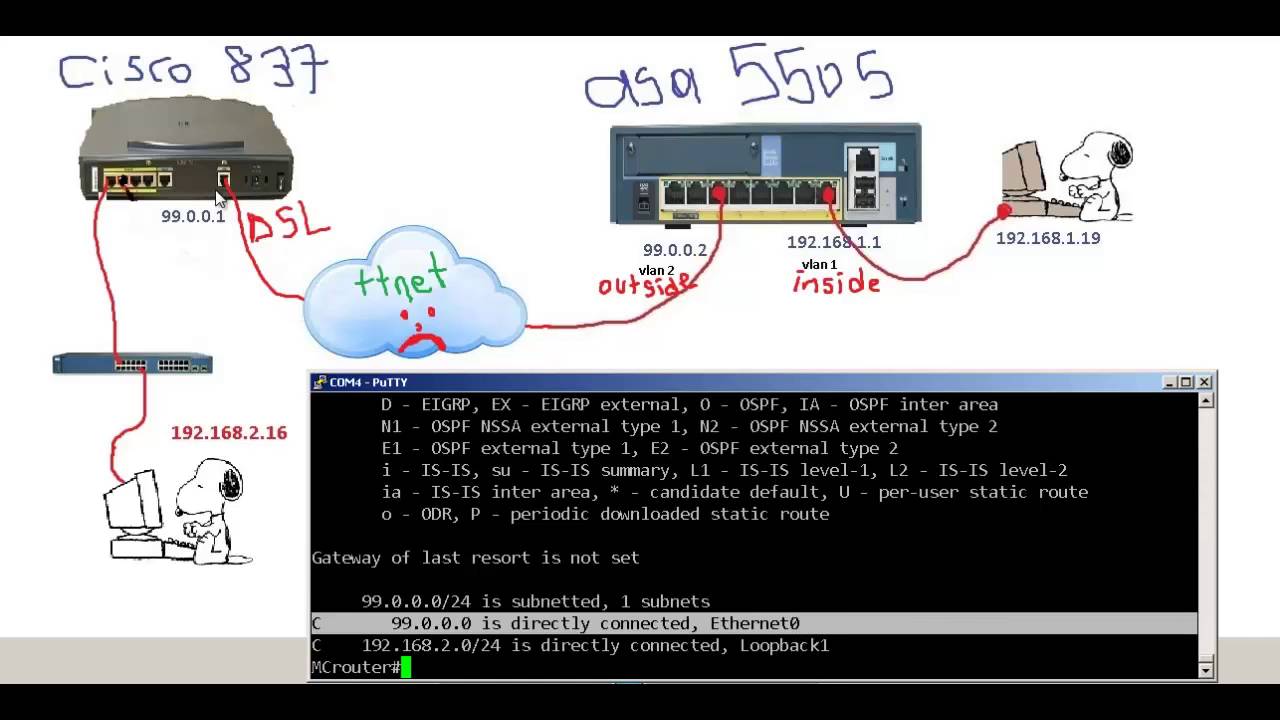
IPsec - 9 - Easy Vpn Nedir ? Server to Remote Client Mode Dynamic CryptoThis tutorial shows you how to configure Cisco Easy IPsec VPN on a IOS router and the Cisco VPN client software. Est. reading time: 3. EZVPN is a technology that lets you form an ISAKMP/IPSEC VPN For EZVPN, all traffic is interesting traffic, it behaves like the old IPSEC VPN client software. This document provides a Easy VPN (EzVPN) sample configuration, using Cisco series, Cisco series, and Cisco series routers.